SECURITY THREATS -A MATTER OF “WHEN” AND NOT “IF” IT WILL HAPPEN
“The art of war teaches us to rely not on the likelihood of the enemy’s not coming, but on our own readiness to receive him.” – Sun Tzu
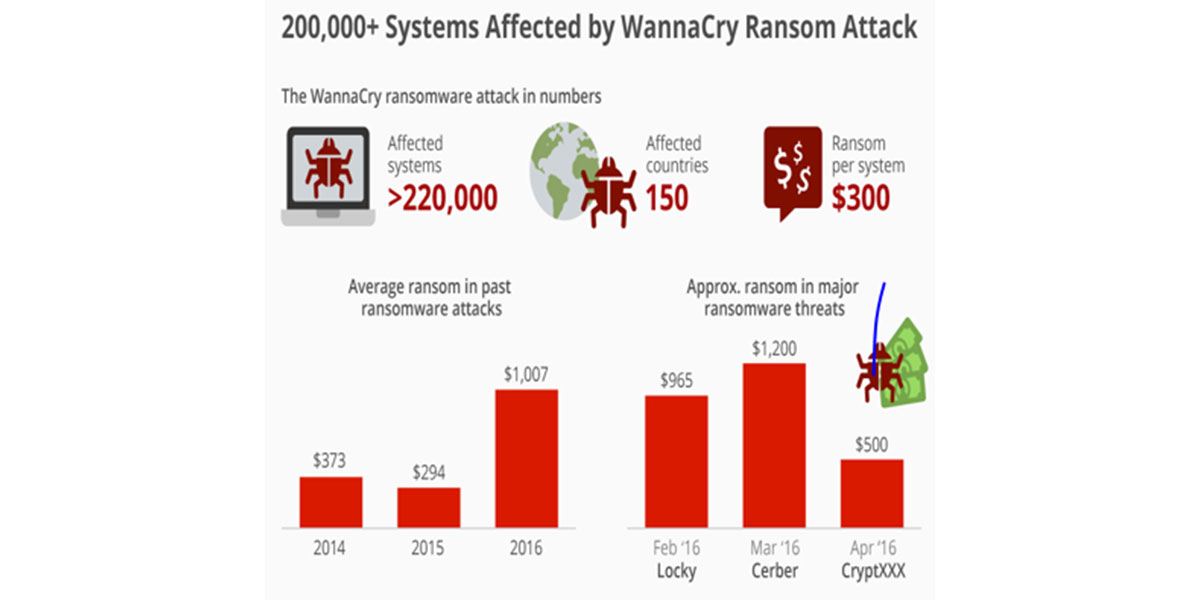
During the attacks from the Crypto Malware WannaCry in May 2017, the world watched astonished the destructive power of the cyber threats and how fast they can spread. The malicious codes makes no distinctions from big players or small shops, it can devastates any one that is not prepared. This particular episode opened the discussion on how protected are companies, how fast they can detect and react upon threats and how big is the impact if the worst happens. This article aims to help the companies – from big enterprises to the one-man-army pizza delivery- to prepare themselves for the new scenarios and put in place a comprehensive plan to reduce the likelihood of an attack as well as responding appropriately when the defenses fails.
The Layered approach
Since the dawn of civilization people have thought they were more secure than they really were. Babylon once felt so secure behind its massive walls and sturdy gates that its king feasted while the Persian army laid siege to the city. The Persians entered early the next morning by damming the river and wading along the riverbed, right into the city. No one had considered that the river that passed beneath the walls—the city’s water supply—could also be its fatal weakness; the king paid for his mistake with his life.
The same paradigm applies to our modern problems with cyber security. One can thinks that “Having a firewall and anti-virus are enough to make your network safe”, but that´s a very innocent assumption.
Attackers will use all available methods to find a way into your network and get your data or make some depending on their motivation. The single focus solutions are not more the answer for the modern threats, traditional anti-virus will not stop specific attacks coming from advanced
malwares, or your firewall may not be effective when a user receive mails with malicious attachments. There are so many different vectors that must be considered that different layers of defense is necessary, however keep in mind there is no silver bullet in the cyber security world. You will still need to get yourself prepared if the bad guys break in.
There are many different suggestions for layered security, however considering the modern threats we must always Bring the automation, machine learn and analytics to the table in order to avoid alert fatigue and floods of false positive/negatives. With that said, here is our layered approach:
Network protection
The firewall is the heart of the network defense layer, it controls traffic based on type, port, source and destination. This is one of the most basic ways to protect the perimeter and the main objective of the stop the malicious traffic right from the beginning. Firewalls have evolved enough to incorporate IPS and traffic inspection services, allowing it to inspect closely each packet and differentiate malicious from legitimate traffic. However malwares and bad actors also evolved and become sophisticate enough to easily by pass this layer of protection and connect to users devices using back doors.
There are manufactures that incorporate more capabilities to the traditional firewalls turning them equipped with ability to filter malicous URLs , techniques to prevent zero-day exploits and block malwares.
End point protection
The antiviruses, along with the firewalls, are part of the traditional layer of defense and much valuable part of the security plan. But it should not be the only technology used to protect network and devices. Antivirus started out with a very specific mission of protecting end points (workstations, servers, smartphones, etc) from malware by relying on comparisons to file signatures. Testing and attack tools such emerged and, over time, were updated to employ the concept of polymorphism; these tools use different—but functionally equivalent—programming logic and encoding mechanisms to change their file signatures and avoid detection.
The fundamental problem with traditional antivirus software is that it is built in the reactive mentality: systems must suffer an attack before it can be stopped, and protection requires a “sacrificial lamb,” or first victim. As a result, legacy antivirus has offered solutions based on that reactionary model. Even the most advanced techniques of signature-based detection, exploit prevention, whitelisting, application controls, and endpoint detection and response, all fall into that victim-first model.
Again the artificial intelligence and machine learn plays a fundamental role by collecting data and learning from patterns, in order to discover new threats.
Vendors leveraging artificial intelligence and behavior analysis to their products are few steps ahead from the old paradigm that requires a “scarified lamb” to discover new threats
Mail and web protection
More than 90% of the targeted attacks start with mail, and these threats are always evolving. The email is definitely the favorite and most efficient tool of attackers in order to deliver malicious payloads. An efficient email protection systems act as a firewall with policies that helps filtering Spams, impostors, bulk, phishing, malwares and undesired content. To protect against sophisticated and threats, the advanced products can offer mechanisms to detect and block malicious attachments and URLs, as well as usage of sandbox to detonate suspicious content. Like the modern anti-malware engines, the machine learning and predictive analysis are key to minimize the risk of a patient-zero-dependent product.
To avoid users surfing unprotected in the wildness of internet the proxies plays an important role. Beyond the expected capabilities of filtering, the web proxy also works as a layer of defense in case a well-crafted phishing mail or sophisticated malware sneaks in and try to call home.
Prevention is ideal, but detection is a must
Attackers can strike across multiple layers and one of these tries will pass through, it is just a matter of “when” and not “if” . In case the worst happens, the ability to detect and remediate is crucial. The tools and capabilities described above can also be used to detect and contain attacks. Network monitors can help collecting and analyzing unusual activity such as: high-bandwidth traffic, stealthy activities, malicious DNS connections and atypical web traffic. All these signals and many other patterns can be collected and interpreted through logs a Security Information and event manager (SIEM) and handled by incident responders.
These incidents must be triaged and classified according to their criticality, as well as checked to avoid false positives. Here again the paradigm of using traditional tools against next-generation that uses artificial intelligence and machine learn to help automate the analysis of security-relevant logs.
After detection, the remediation is another key step and where the tough work starts. As soon as the infected system is detected it is imperative that malwares are remove or quarantine for in depth investigation in order to determine what kind of damage, how extensive and if remediation was effective.
Managni systems can support you to find the right strategy for your organization in order to protect, detect and respond appropriately to the modern threats. We have a team of seasoned experts ready to analyze your case and suggest the right solution.