Our philosophy is to stay miles ahead of malicious actors and advanced threats they deploy. Staying ahead of hackers to detect and prevent threats require better visibility into the network. As the networks grow, you start to loose control. We work all the top vendors in the security space and have created a compelling innovative reference architecture that not only allows you to get the best of the breed security products available in the industry, but also seamlessly work together as a solution, that spans , across laptops, virtual desktops, servers, web, email traffic, mobile devices, etc.
We help organizations defend against advanced persistent threats, detect anomalies using security analytics, comply to industry mandates, automate processes and secure devices across the network. Following different types of security solutions are used to get the ultimate protection that your Organization deserves.
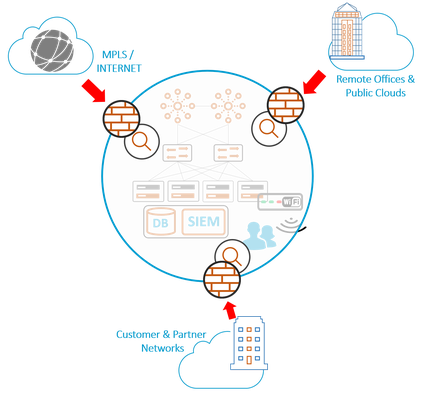
Perimeter Security

Email Security
Intruders can create havoc if proper email security is not deployed. Hackers have a easy target trying to make inroads in the company’s network with trying to break in through email-borne threats such as ransomware, phishing and malicious links and attachments. ManagNI experts recommend protecting email using a cloud SaaS service or in-house appliance.
Quarantines includes
- Virus emails
- Fishing/ransomware
- Adult Content
- Bulk
- Spam
- Imposter
- Domain Reputation
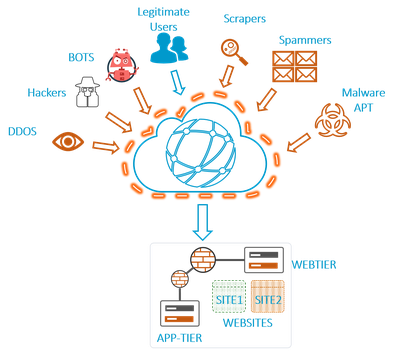
Web Security
Next-gen protection against ransomware and malicious attacks, Anti-malware, Anti-exploit, Root cause analysis.
- Web Application Firewalls (WAF)
- Data Loss Prevention (DLP) System
- URL, AV and Malware

End Point Security
Securing the endpoints is a key aspect of the overall security architecture that ManagNI recommends.
Virus can be a script, or macro designed to cause damage, steal personal information, modify data, send e-mail, display messages,it spreads by copying itself.ManagNI recommends using latest machine based learning technology for AntiVirus software to stay ahead in the Endpoint Security space.
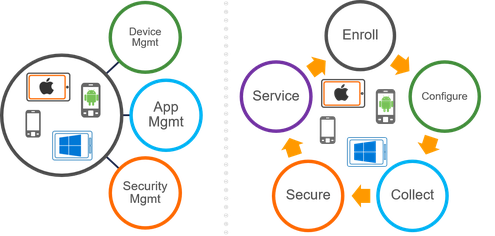
Mobile Device Security
Securiing the mobile device is a key aspect of security in the enterprise. ManagNI recommends using the best MDM vendor which offers comprehensive Mobile Device Security, spanning across :
- Device Auto Provisioning
- Mobile App Management
- Mobile Identity
- Mobile Content Management
- Data Containment (Data Leak Protection)
- Device Virtualization/Containerization

Security Checks and Monitoring
Periodic security checks and monitoring is key to ensuring what ports, systems are exposed to security threats. Having the right log management tool is key to summarizing these threats over a period of time to get the historical context.
- Vulnerability Tests
- Penetration Tests
- Security Incident Event Management (SIEM) system
- Authentication & Federation Controls
- Compliance, Governance and Auditing
